Docker Setup¶
Danger
Docker is not officially supported at the moment and not recommended for production use unless you are an advanced docker user and very comfortable managing and troubleshooting docker.
Please read the docker install considerations before continuing.
Install Docker¶
Install docker.
Please keep in mind that the docker package is usually called docker.io in debian based distros including ubuntu
Create the DNS A records¶
Warning
All 3 domain names have to be at the same subdomain level because you only get one LetsEncrypt wildcard cert, and it'll only apply to that level of DNS name.
We'll be using example.com as our domain for this example.
Info
The RMM uses 3 different sites. The Vue frontend e.g. rmm.example.com which is where you'll be accessing your RMM from the browser, the REST backend e.g. api.example.com and MeshCentral e.g. mesh.example.com
- Get the public IP of your server with
curl https://icanhazip.tacticalrmm.io - Open the DNS manager of wherever the domain you purchased is hosted.
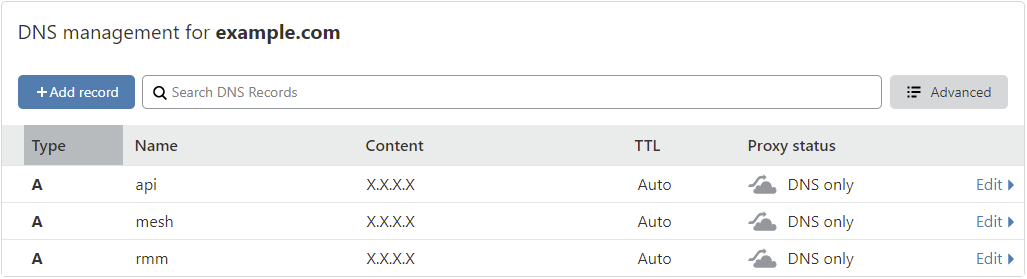
- Create 3 A records:
rmm,apiandmeshand point them to the public IP of your server:
Acquire Let's Encrypt wildcard certs with Certbot¶
Warning
If the Let's Encrypt wildcard certificates are not provided, a self-signed certificate will be generated and most agent functions won't work.
1 ) Install Certbot
sudo apt-get install certbot
2 ) Generate the wildcard Let's Encrypt certificates
We're using the DNS-01 challenge method.
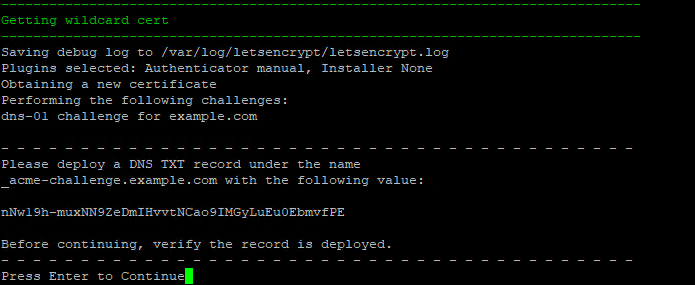
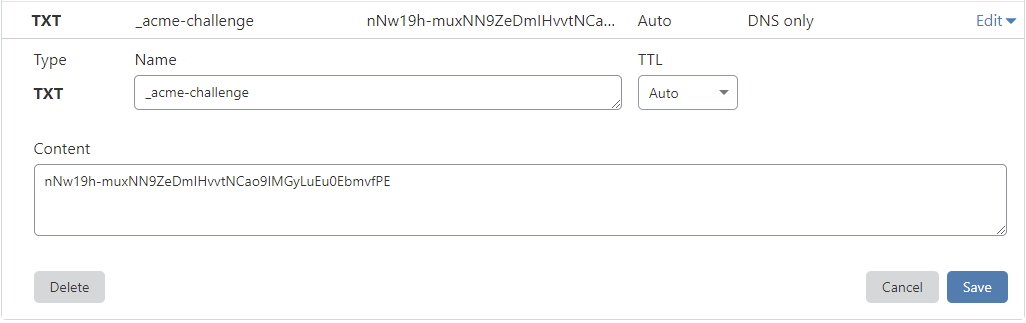
3 ) Deploy the TXT record in your DNS manager
Warning
TXT records can take anywhere from 1 minute to a few hours to propagate depending on your DNS provider.
You should verify the TXT record has been deployed first before pressing Enter.
A quick way to check is with the following command:
dig -t txt _acme-challenge.example.com
or test using: https://viewdns.info/dnsrecord/ Enter: _acme-challenge.example.com
4 ) Request ncrypt wildcard cert
sudo certbot certonly --manual -d *.example.com --agree-tos --no-bootstrap --preferred-challenges dns
Note
Replace example.com with your root domain.
Configure DNS and firewall¶
You will need to add DNS entries so that the three subdomains resolve to the IP of the docker host. There is a reverse proxy running that will route the hostnames to the correct container. On the host, you will need to ensure the firewall is open on TCP port 443.
Setting up the environment¶
Get the docker-compose and .env.example file on the host you which to install on
wget https://raw.githubusercontent.com/amidaware/tacticalrmm/master/docker/docker-compose.yml
wget https://raw.githubusercontent.com/amidaware/tacticalrmm/master/docker/.env.example
mv .env.example .env
Change the values in .env to match your environment.
When supplying certificates through Let's Encrypt, see the section below about base64 encoding the certificate files.
Base64 encoding certificates to pass as env variables¶
Use the below command to add the the correct values to the .env.
Running this command multiple times will add redundant entries, so those will need to be removed.
Let's Encrypt certs paths are below. Replace ${rootdomain} with your own.
public key
/etc/letsencrypt/live/${rootdomain}/fullchain.pem
private key
/etc/letsencrypt/live/${rootdomain}/privkey.pem
echo "CERT_PUB_KEY=$(sudo base64 -w 0 /path/to/pub/key)" >> .env
echo "CERT_PRIV_KEY=$(sudo base64 -w 0 /path/to/priv/key)" >> .env
Starting the environment¶
Run the below command to start the environment:
docker compose up -d
Removing the -d will start the containers in the foreground and is useful for debugging.
If you get a error saying you don't have permission you can add yourself to the docker group with:
sudo usermod -aG docker [user]
Login¶
Navigate to https://rmm.example.com and login with the username/password you created during install.
Once logged in, you will be redirected to the initial setup page.
Create your first client/site and choose the default timezone.
Note About Backups¶
The backup script does not work with docker. To backup your install use standard docker backup/restore processes.
Or, you can look at larseberhardt/TRMM-Docker-Backup-Script.